Understanding Bearer Tokens, JWTs, and Opaque Tokens: A Comprehensive Comparison
April 12, 2025
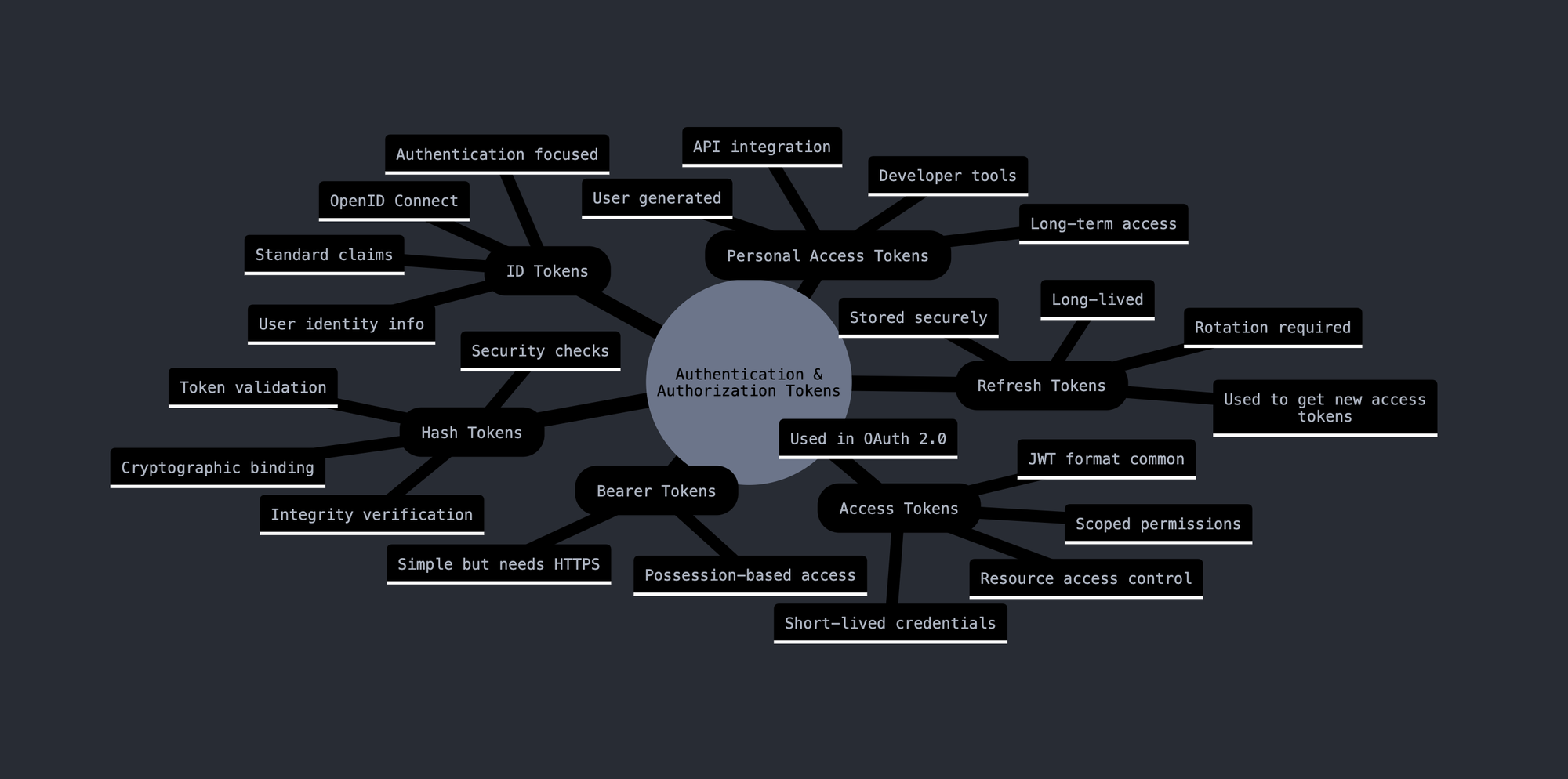
Bearer Tokens
JWT
Opaque Tokens
Authentication
Security
Web Development
This article provides a detailed comparison of Bearer Tokens, JWTs, and Opaque Tokens, highlighting their definitions, structures, usage, benefits, drawbacks, and key differences to help developers choose the right authentication mechanism for their applications.
Bearer Tokens, JWT, and Opaque Tokens: A Comparison
Understanding the differences between Bearer Tokens, JWTs (JSON Web Tokens), and Opaque Tokens is essential for implementing secure and efficient authentication mechanisms in your applications. Here's a detailed comparison:
Bearer Tokens
- Definition: A Bearer Token is a security token where the party in possession of the token (the "bearer") is granted access to a resource without further identification.
- Structure: Opaque, meaning it does not contain any user or claim information within the token itself.
- Usage: Primarily used for authentication. The client includes the token in the HTTP Authorization header to access protected resources.
- Benefits: Simple to implement, flexible, and secure since clients cannot tamper with the token's content.
- Drawbacks: Stateless, meaning tokens cannot be revoked without additional infrastructure. Lack of standardization can lead to inconsistency.
JWT (JSON Web Tokens)
- Definition: A JWT is a compact, URL-safe token that represents claims to be transferred between two parties. It is structured and self-contained.
- Structure: Composed of three parts: Header (metadata), Payload (claims), and Signature (for verification).
- Usage: Used for both authentication and information exchange. Ideal for stateless sessions where the token carries all necessary information.
- Benefits: Compact, self-contained, and scalable. Suitable for modern web applications.
- Drawbacks: Once issued, JWTs cannot be easily revoked until they expire. Increasing payload size can affect performance.
Opaque Tokens
- Definition: Opaque Tokens are similar to Bearer Tokens in that they are opaque and do not contain any user or claim information within the token itself.
- Structure: Opaque, meaning the token is a random string that must be validated by the server.
- Usage: Used for authentication, where the server must validate the token by querying a database or other storage mechanism.
- Benefits: Secure since the token itself does not contain any sensitive information. Can be revoked by the server.
- Drawbacks: Requires additional server-side infrastructure for validation and revocation. Less efficient than JWTs for stateless applications.
Key Differences
| Feature | Bearer Token | JWT | Opaque Token |
|---|---|---|---|
| Structure | Opaque | Structured (Header, Payload, Signature) | Opaque |
| Information | None | Contains claims and user information | None |
| Usage | Authentication | Authentication and Information Exchange | Authentication |
| Revocation | Requires additional infrastructure | Cannot be revoked until expiration | Can be revoked by the server |
| Security | Secure, but requires HTTPS | Secure with signature, but payload can be large | Secure, but requires server-side validation |
When to Use Each
- Use Bearer Tokens: When you need a simple and flexible authentication mechanism, and you have infrastructure in place to manage token revocation.
- Use JWTs: When you need a self-contained token that can carry information between parties, and you require a compact token that can be passed around easily.
- Use Opaque Tokens: When you need a secure token that can be revoked by the server, and you have the necessary server-side infrastructure for validation.
By understanding the strengths and weaknesses of each token type, you can choose the one that best fits your application's needs. Always follow best practices such as using HTTPS, implementing token expiration, and securely storing tokens to ensure the security of your application.
Sources
A Guide to Bearer Tokens: JWT vs. Opaque Tokens - Permit.io
Learn the key differences between JWT and opaque bearer tokens, covering how they work, when to use each, and how they impact API authentication ...
JWT vs. Bearer Token: Understanding the Difference - Apidog
JWTs offer a structured, self-contained way to transmit information, while Bearer tokens provide a simple and flexible authentication method.
What's the difference between a Bearer Token and JWT? I thought ...
You can use a JWT as a Bearer token, but since it's only base64 encoded, you can pull out that payload data. A truly opaque Bearer token will be meaningless to ...