semgrep
by semgrepSemgrep MCP Server for Code Scanning
Overview
The Semgrep MCP Server is a beta implementation that integrates Semgrep, a powerful static analysis tool, with the Model Context Protocol (MCP). This server allows you to scan code for security vulnerabilities directly within LLMs, AI agents, and coding tools like Cursor. It provides a comprehensive interface to Semgrep, enabling code scanning, rule customization, and result analysis.
Features
- Code Scanning: Scan code snippets or entire directories for security vulnerabilities.
- Customization: List, create, and manage custom Semgrep rules.
- Result Analysis: Analyze, filter, and export scan results in various formats.
- Advanced Tools: Compare scan results to identify new and fixed issues.
Demo
Installation
CLI
- Install
uvusing their installation instructions. - Ensure Python 3.13+ is installed.
- Clone the repository.
- Install Semgrep:
shell pip install semgrep
Docker
docker build -t mcp-server .
Usage
CLI
uv run mcp run server.py -t sse
Docker
docker run -p 8000:8000 mcp-server
Or use the pre-built image:
docker run -p 8000:8000 ghcr.io/semgrep/mcp:latest
Creating Your Own Client
from mcp.client import Client
client = Client()
client.connect("localhost:8000")
# Scan code for security issues
results = client.call_tool("semgrep_scan", {
"code": "def get_user(user_id):\n return User.objects.get(id=user_id)",
"language": "python"
})
Cursor Plugin
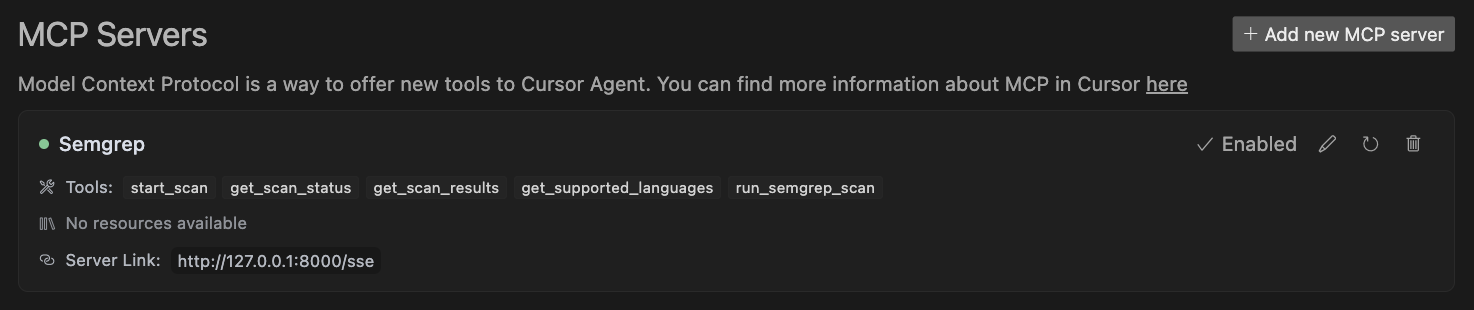
- Go to Cursor > Settings > Cursor Settings.
- Choose the
MCPtab. - Click "Add new MCP server".
- Name:
Semgrep, Type:sse, Server URL:http://127.0.0.1:8000/sse. - Ensure the MCP server is enabled.
Advanced Usage
# Scan an entire directory
results = client.call_tool("scan_directory", {
"path": "/path/to/code",
"config": "p/security-audit"
})
# Filter results by severity
filtered = client.call_tool("filter_results", {
"results_file": "/path/to/results.json",
"severity": "ERROR"
})
Development
Running the Development Server
uv run mcp dev server.py
By default, the server runs on http://localhost:3000 with the inspector server on http://localhost:5173.
Note: When opening the inspector server, add query parameters to the URL to increase the default timeout:
http://localhost:5173/?timeout=300000
Community & Related Projects
Core Technologies
- Semgrep - The underlying static analysis engine.
- Model Context Protocol (MCP) - The protocol enabling AI agent communication.
Similar Tools
- semgrep-vscode - Official VSCode extension for Semgrep.
- semgrep-intellij - IntelliJ plugin for Semgrep.
Community Projects
- semgrep-rules - Official collection of Semgrep rules.
- mcp-server-semgrep - Original inspiration by Szowesgad and stefanskiasan.
MCP Server Registries
About
The Semgrep MCP Server is a beta project that integrates Semgrep with the MCP framework, enabling code scanning within LLMs and AI agents. It is licensed under the MIT license and actively developed by the Semgrep community.
Topics
Resources
Contributors
Languages
- Python (96.8%)
- Dockerfile (3.2%)