stumason_get_mcp_keys
by StuMasonSecure API Key Loader for Cursor MCP Servers
Overview
get-mcp-keys is a lightweight utility designed to securely load API keys for Cursor MCP servers from your home directory. It prevents accidental exposure of secrets in repositories, ensuring your credentials remain safe while maintaining seamless integration with AI coding assistants.
The Problem
When using Cursor AI and other AI coding assistants with MCP servers, API keys are often stored in the ./cursor/mcp.json file. This poses a significant security risk, as accidental commits can expose these keys in your Git history.
The Solution
get-mcp-keys addresses this issue by loading your API keys from a secure file in your home directory, keeping them out of your repositories entirely.
Quick Start
1. Create a .mcprc file in your home directory
touch ~/.mcprc
chmod 600 ~/.mcprc # Make it readable only by you
2. Add your API keys to the file
# ~/.mcprc
FIRECRAWL_API_KEY="your_actual_api_key_here"
BRAVE_API_KEY="another_secret_key_here"
# Add any other MCP server keys you use
3. Update your MCP configuration to use get-mcp-keys
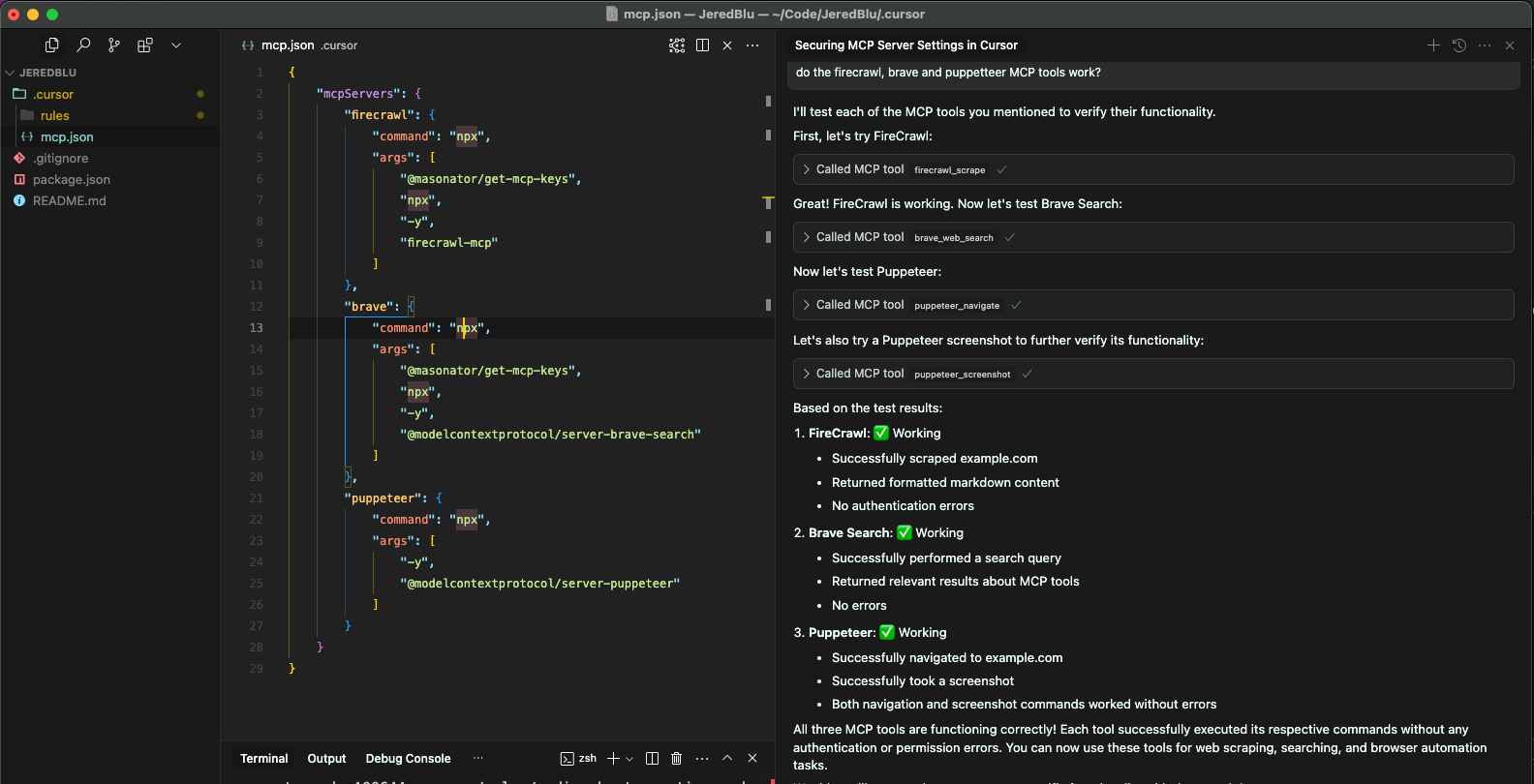
{
"mcpServers": {
"firecrawl": {
"command": "npx",
"args": [\
"@masonator/get-mcp-keys", // 🔐\
"npx",\
"-y",\
"firecrawl-mcp"\
]
}
}
}
That's it! The get-mcp-keys utility will:
- Load your API keys from ~/.mcprc
- Inject them as environment variables
- Run your MCP server command with the keys available
Security
- Your API keys stay in your home directory
- Keys are never committed to repositories
- Keys are loaded only when needed
- Debug output shows only first/last few characters of keys
Supported MCP Servers
Works with any MCP server that needs environment variables, including:
- FireCrawl
- Brave Search
- Supabase
- And any other MCP servers you configure!
How It Works
get-mcp-keys reads your .mcprc file, adds those environment variables to the current environment, and then executes whatever command you specify after it in the args list. It's simple yet effective!
License
MIT
⭐ If this saved you from committing your keys, star the repo!
About
A lightweight utility that securely loads API keys for Cursor MCP servers from your home directory, preventing accidental exposure of secrets in repositories. Keep your credentials safe while maintaining seamless integration with AI coding assistants.
Topics
nodejs api dotenv cursor keys key-management devsecops secrets-management credential- mcp-server mcp-ser
Resources
Stars
Watchers
Forks
No packages published
